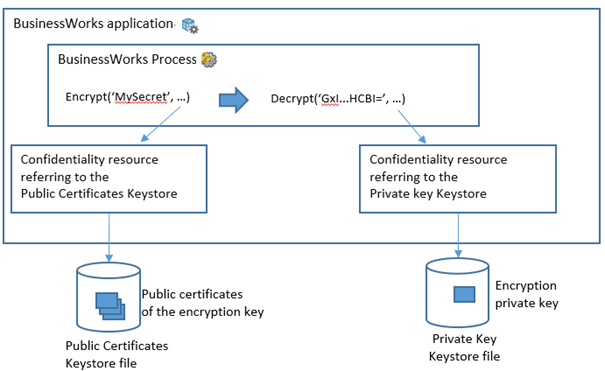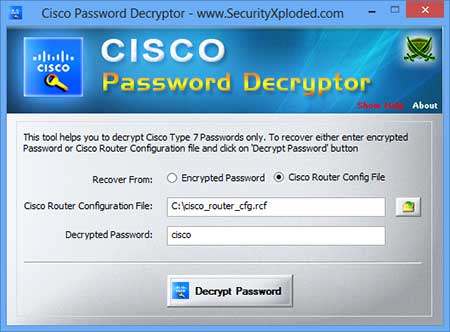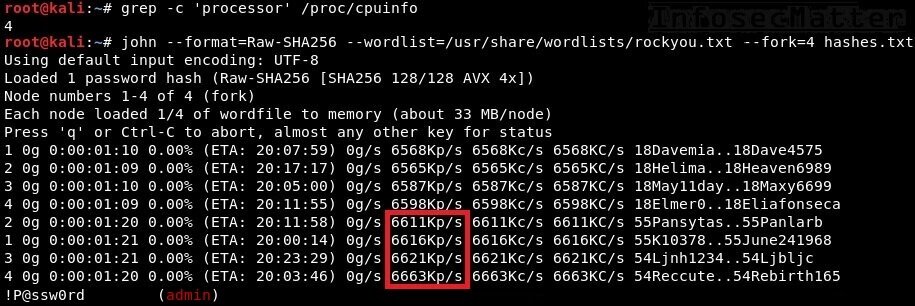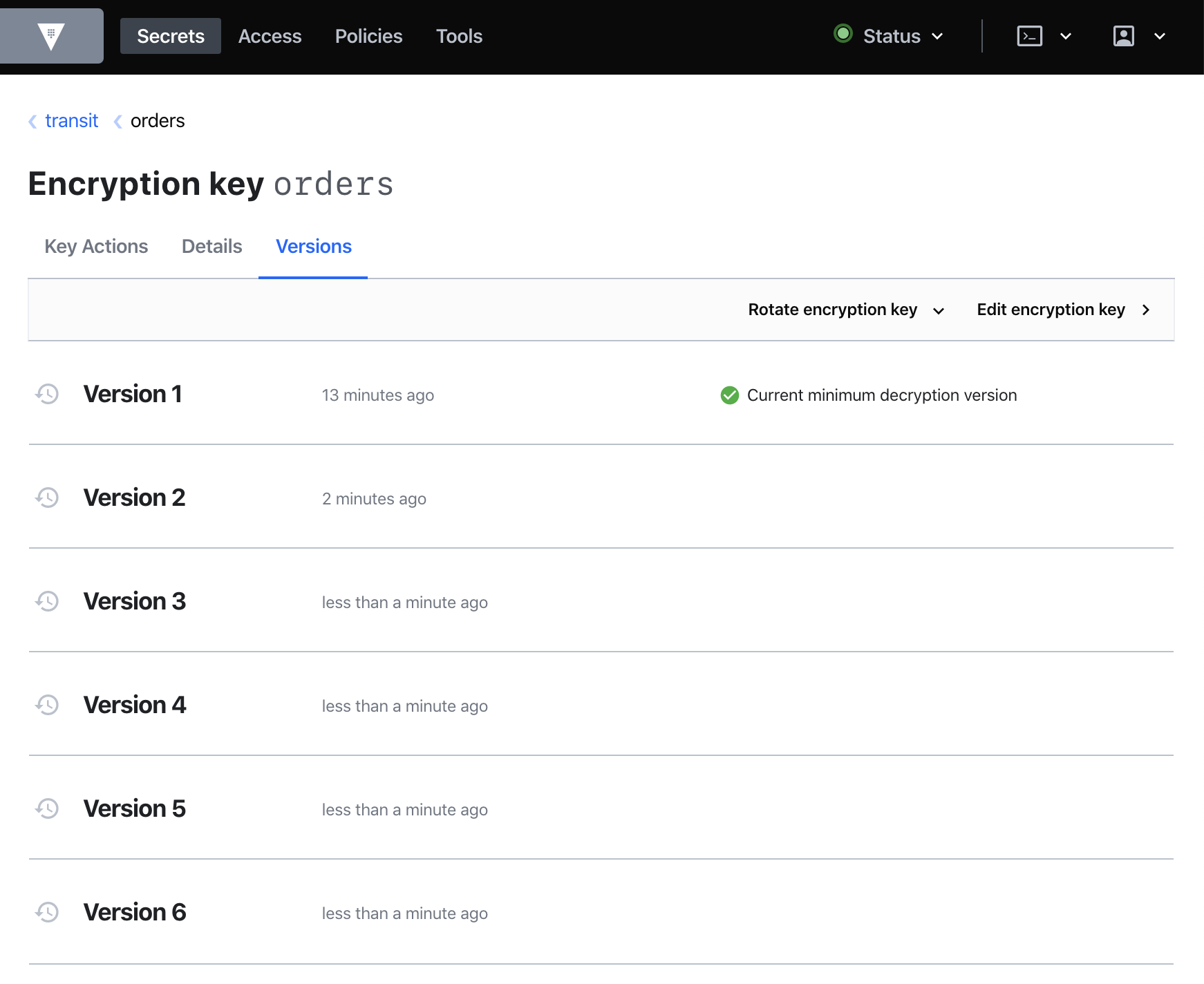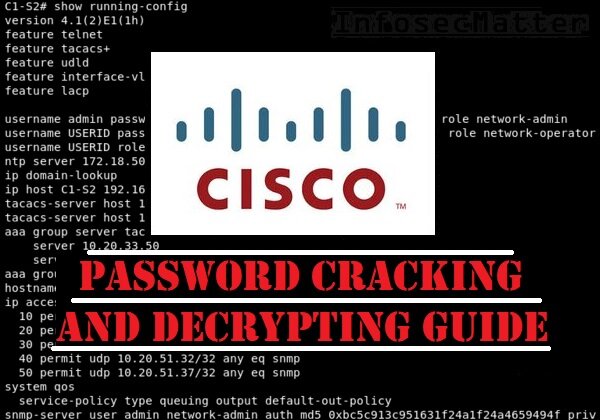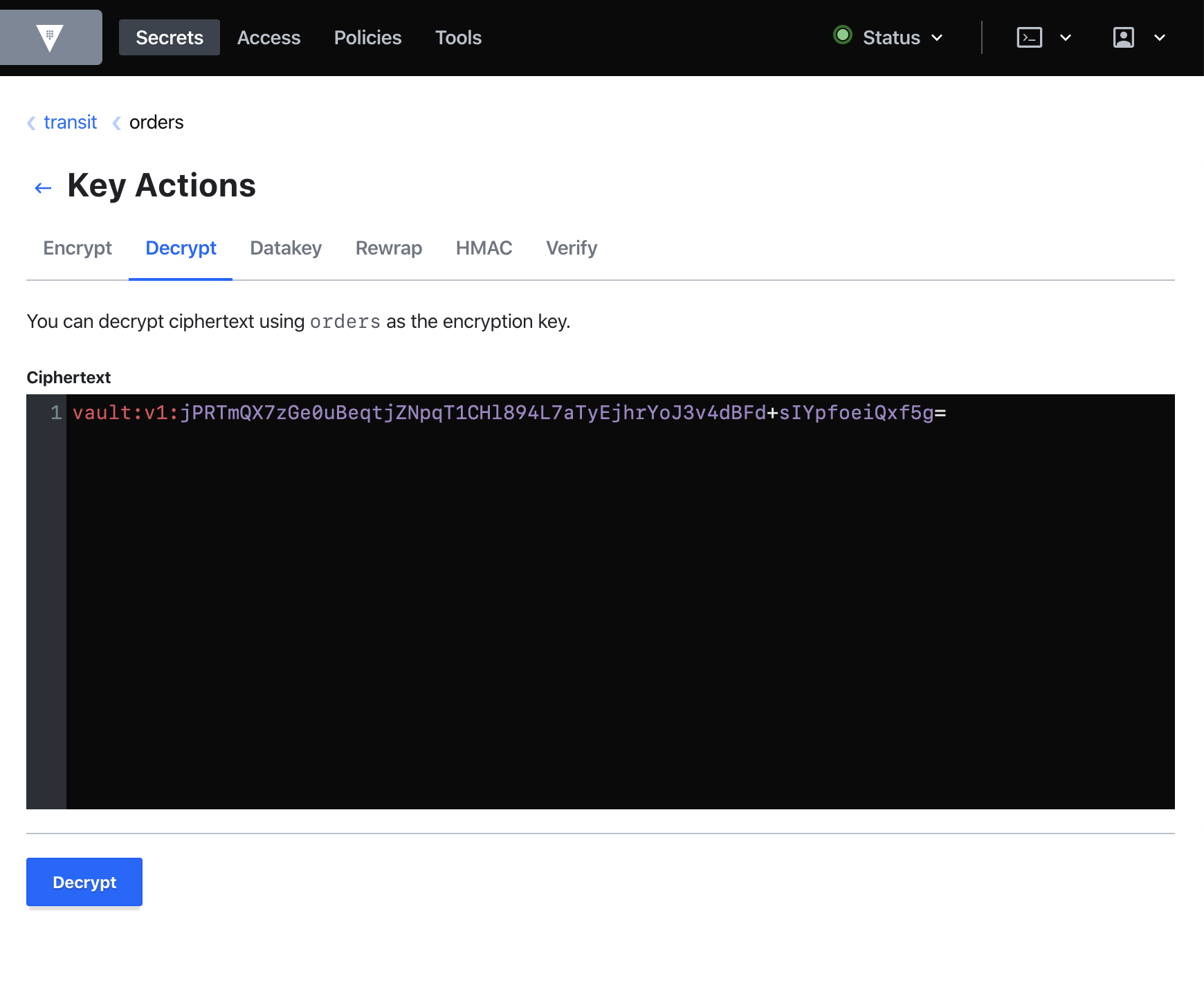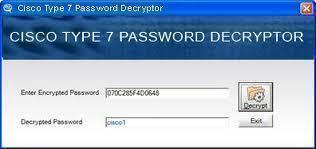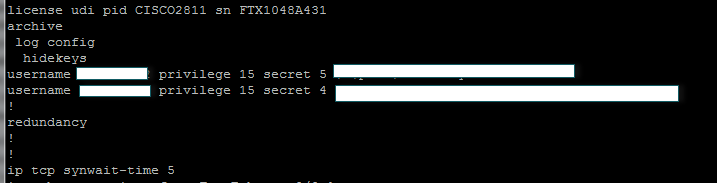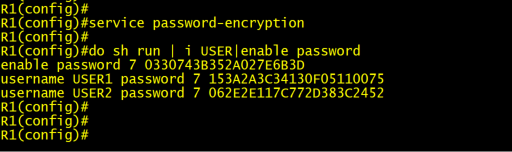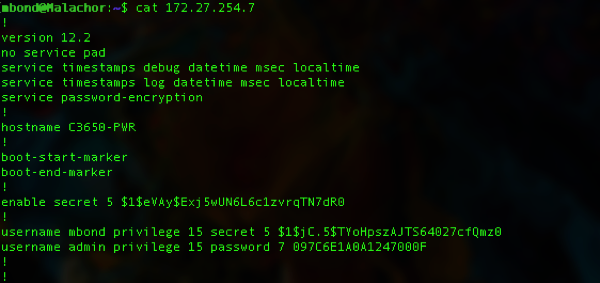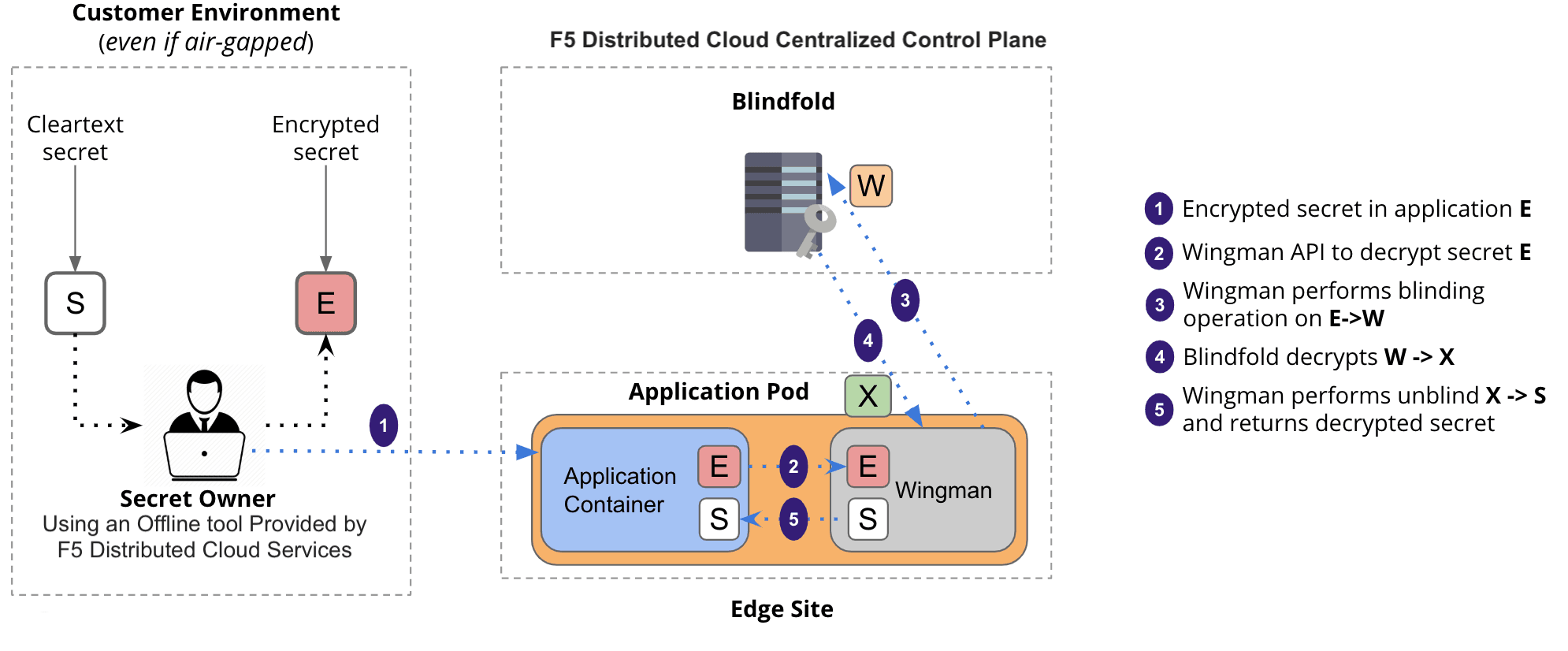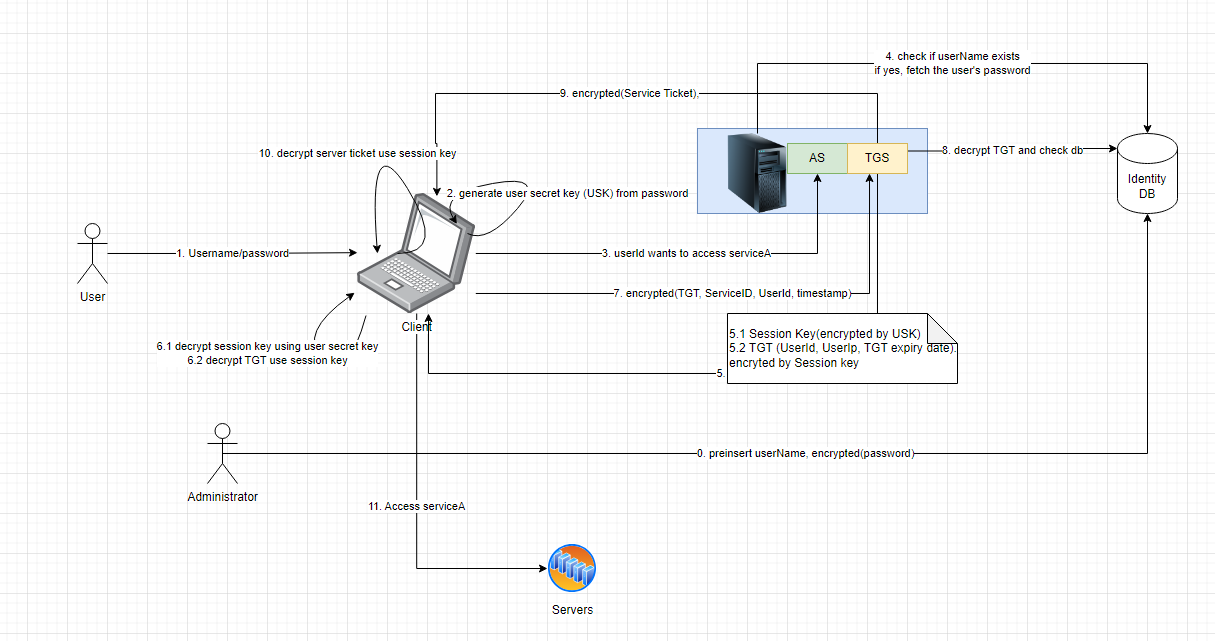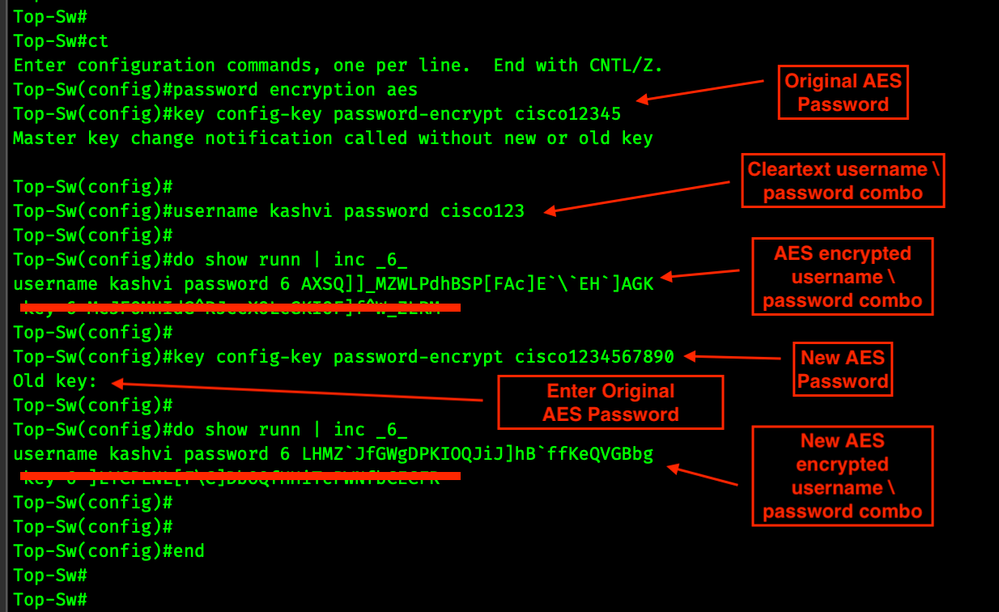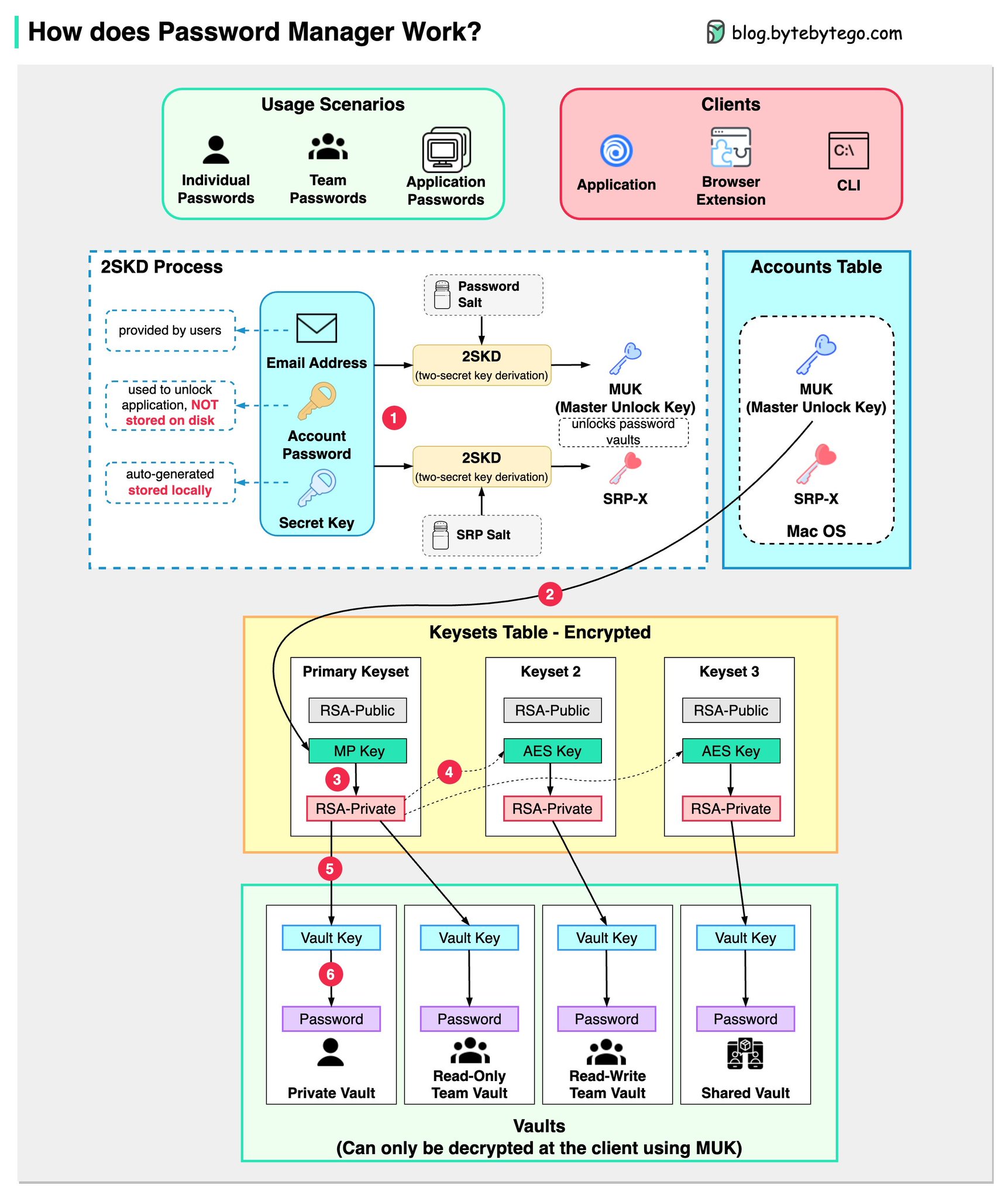
Alex Xu on X: "How does a Password Manager such as 1Password or Lastpass work? How does it keep our passwords safe? The diagram below shows how a typical password manager works.

5: Structure of Service Program P : secret k P is embedded in P which... | Download Scientific Diagram
Decrypt-TFSSecretVariables/Decrypt-TFSSecretVariables.ps1 at master · fox-it/Decrypt-TFSSecretVariables · GitHub