Indian Mujahideen: The Secret Jihad in South Asia: Krishankant, S. M.: 9789380318653: Amazon.com: Books

According to French "terrorism expert" Roland Jacquard, this manual, called "Mujahideen Secrets 2" is used by terrorists to avoid being tracked on the internet : r/programming

Indian Mujahideen: The Secret Jihad in South Asia: Krishankant, S. M.: 9789380318653: Amazon.com: Books

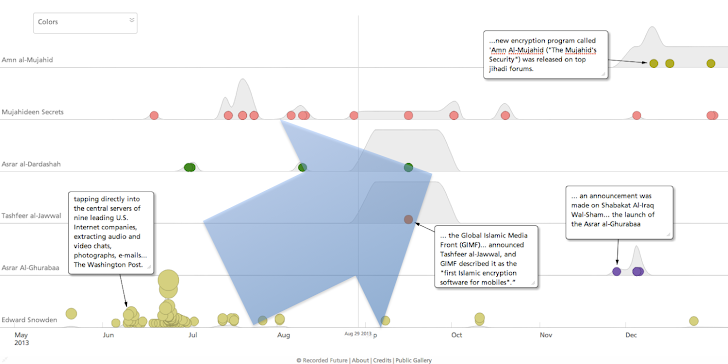
Al-Qaeda's Embrace Of Encryption Technology - Part II: 2011-2014, And The Impact Of Edward Snowden | MEMRI