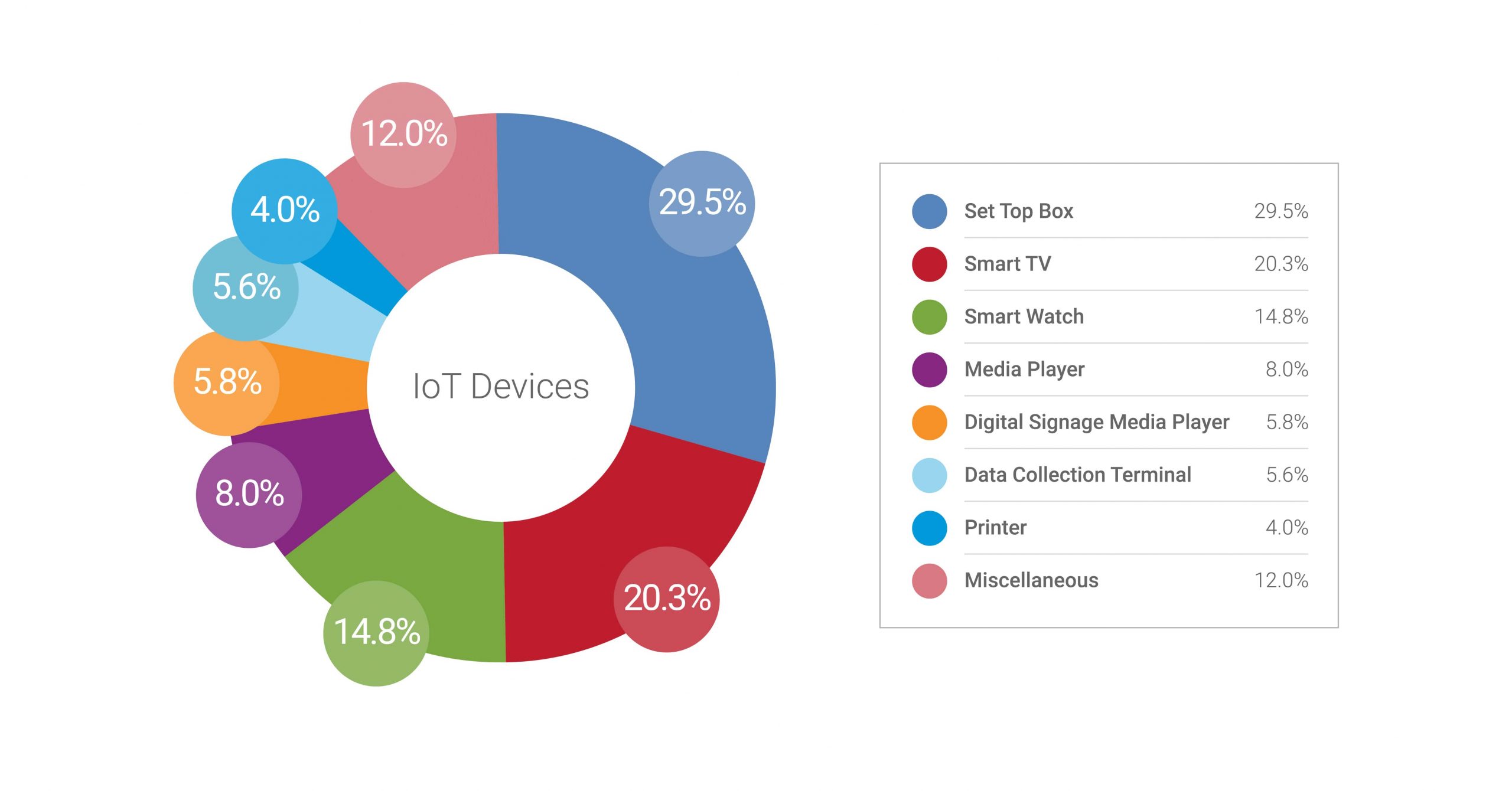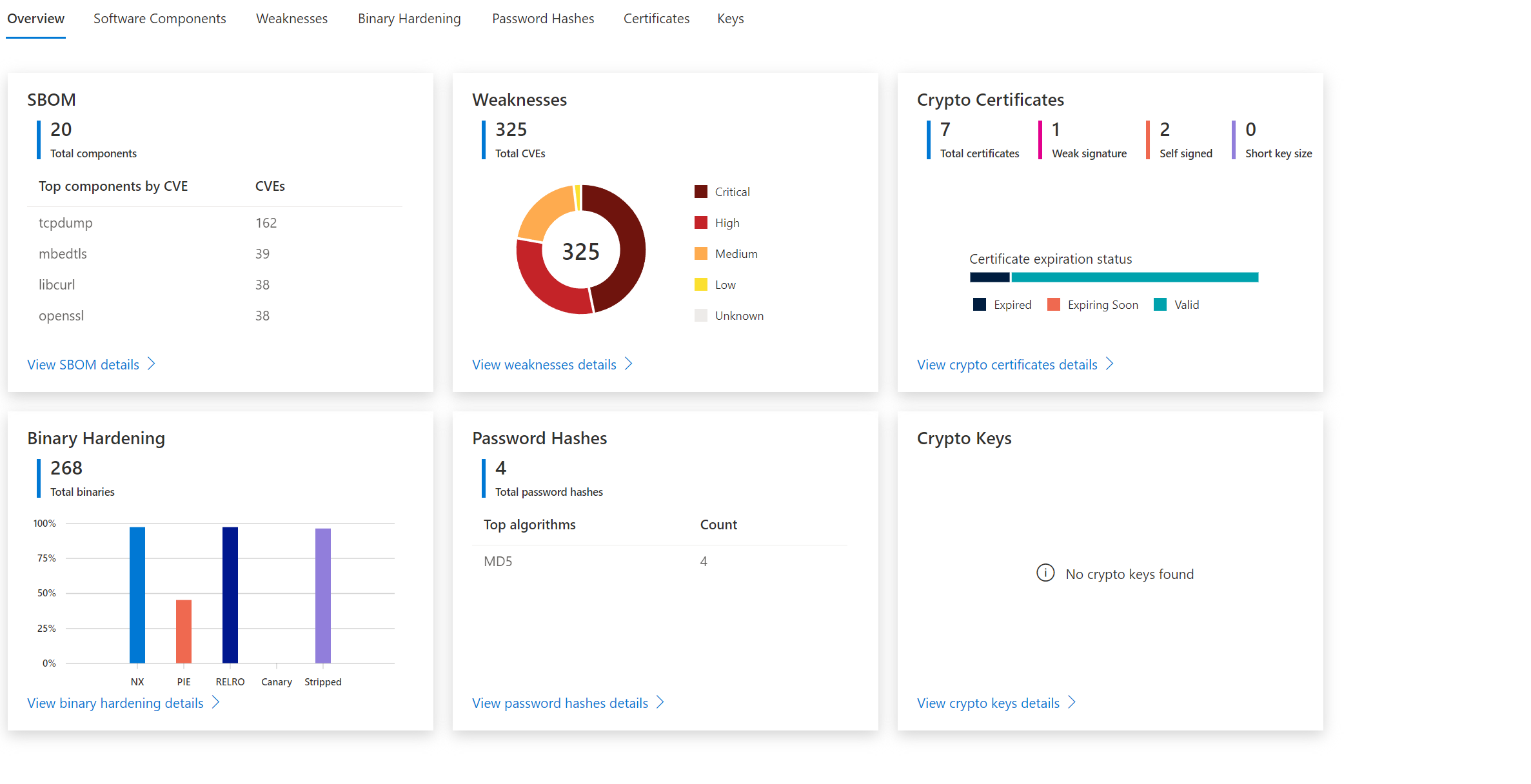
How to use Defender for IoT firmware Scanning for checking potential security vulnerabilities and weaknesses

Uncovering Trickbot's use of IoT devices in command-and-control infrastructure | Microsoft Security Blog

Electronics | Free Full-Text | Analysis of Consumer IoT Device Vulnerability Quantification Frameworks
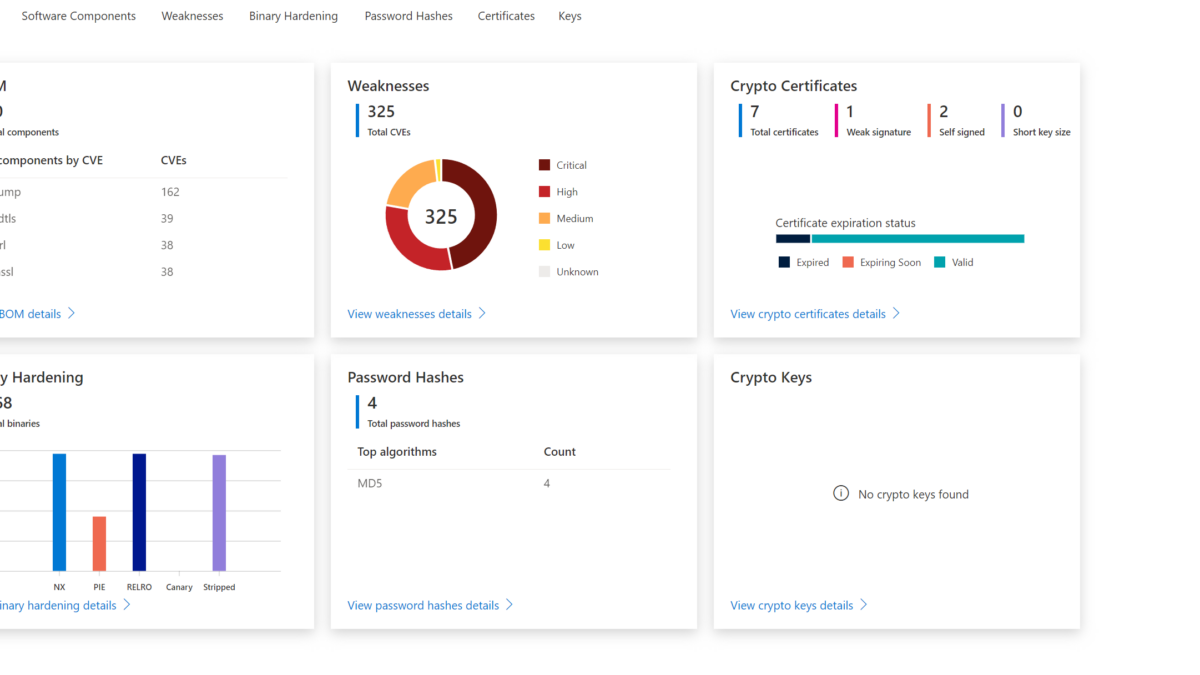
How to use Defender for IoT firmware Scanning for checking potential security vulnerabilities and weaknesses

Internet of things (IoT) and common vulnerability scoring system (CVSS) | Download Scientific Diagram
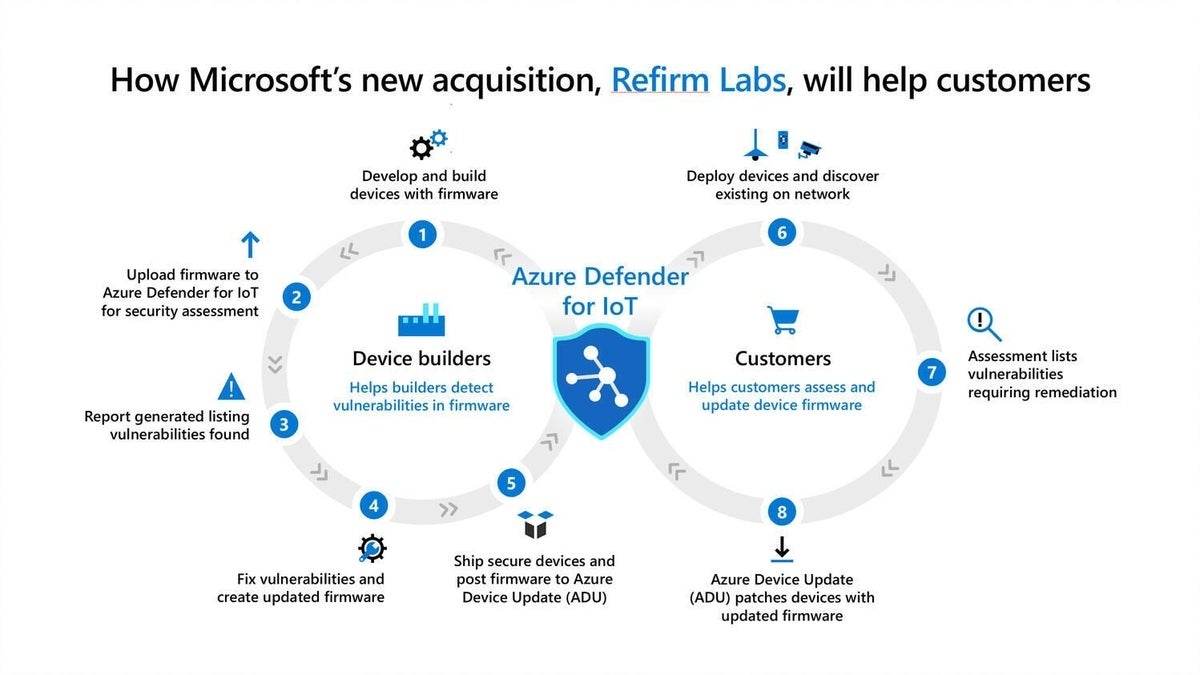
Microsoft's new security tool will discover firmware vulnerabilities, and more, in PCs and IoT devices | TechRepublic

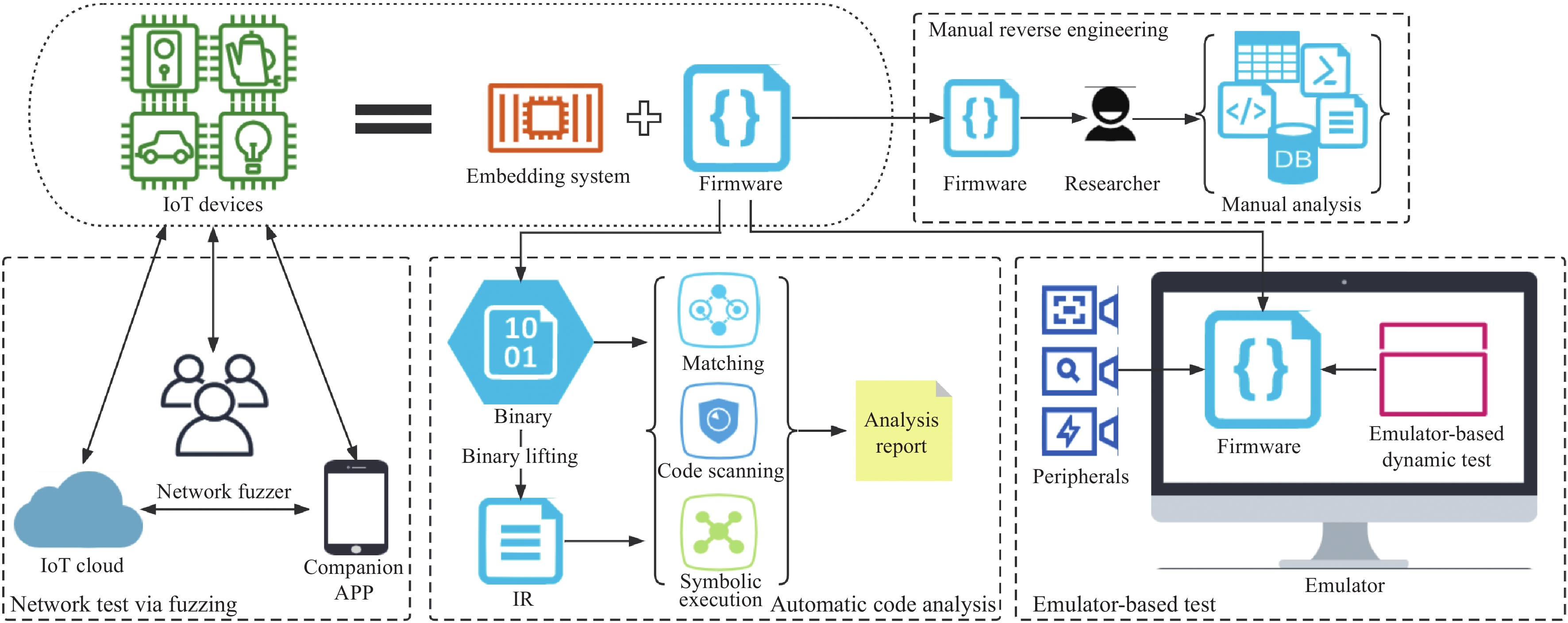
A survey on IoT & embedded device firmware security: architecture, extraction techniques, and vulnerability analysis frameworks | Discover Internet of Things
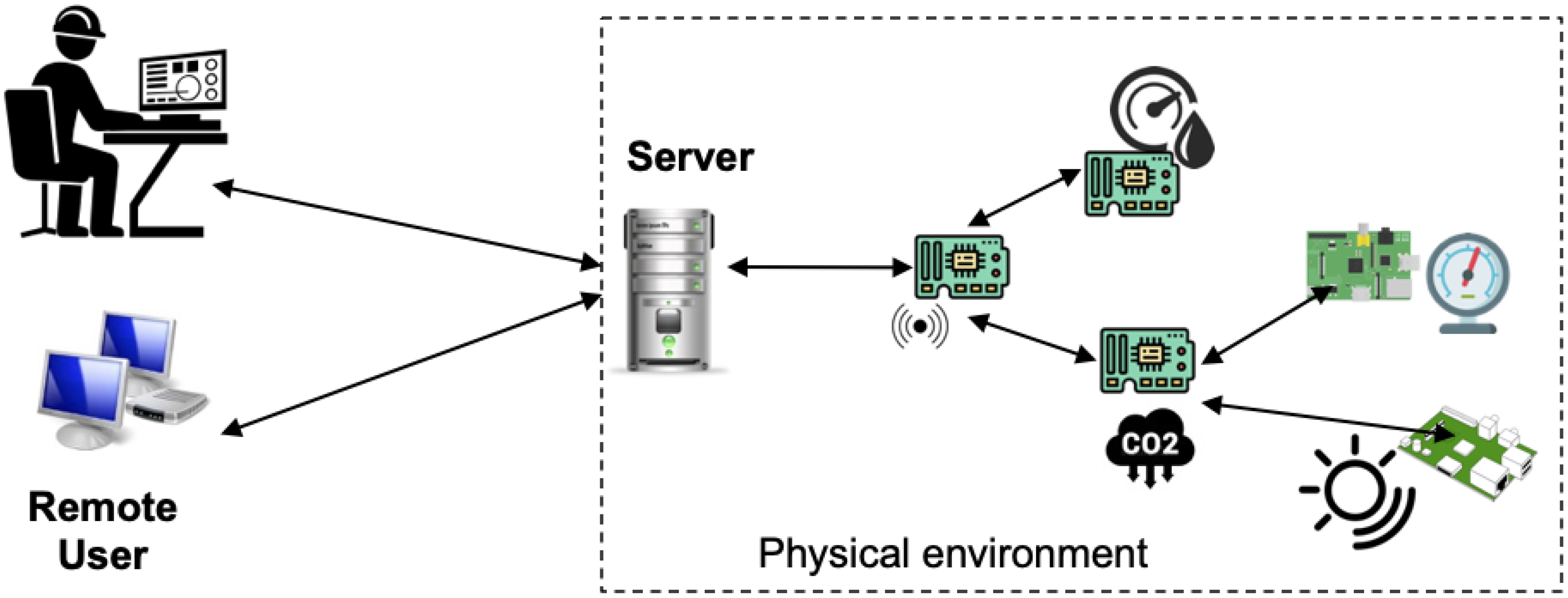
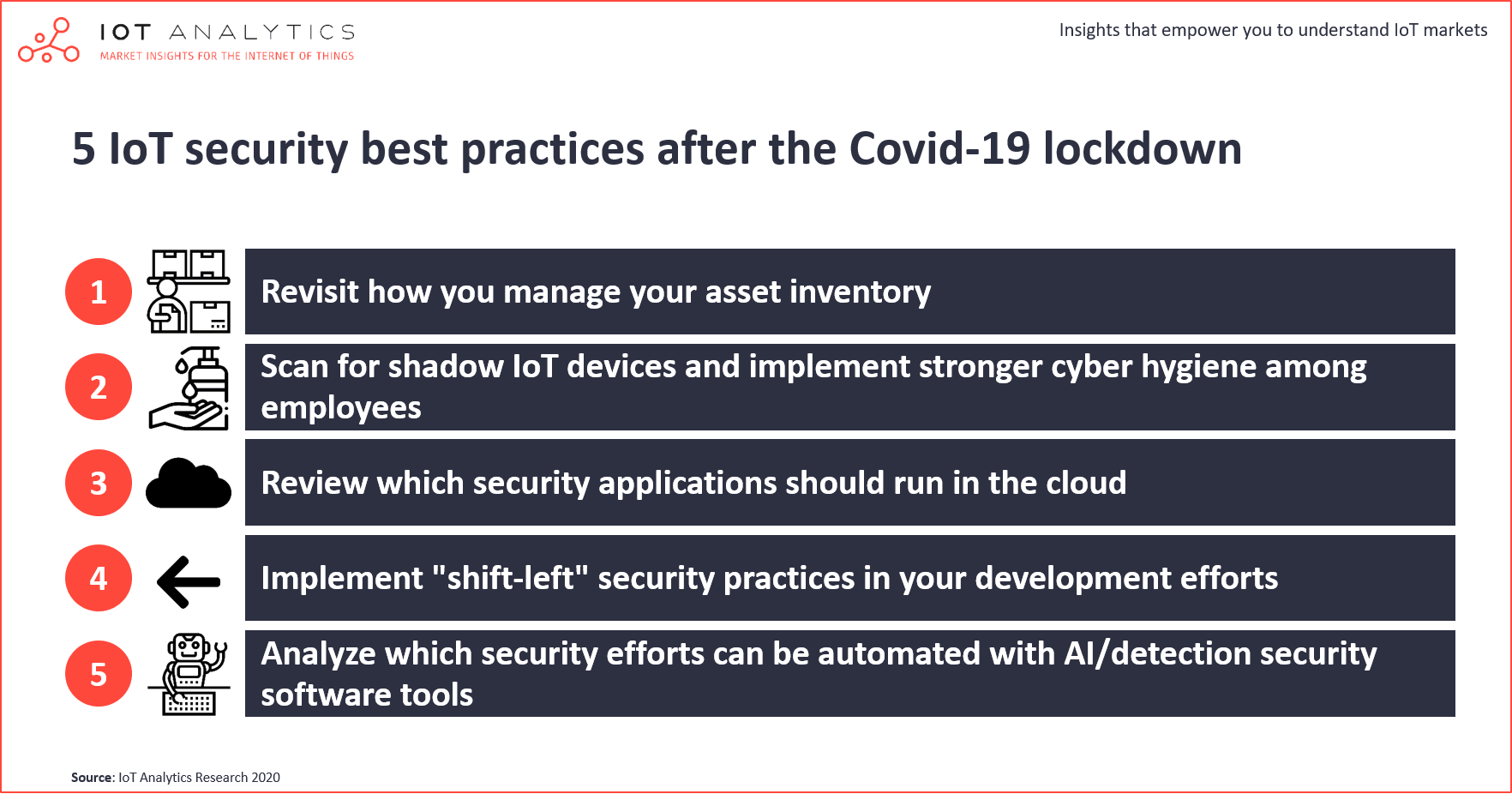

![5 Challenges of IoT Security and Tips to Secure Your Devices [Infographic] - SecurityHQ 5 Challenges of IoT Security and Tips to Secure Your Devices [Infographic] - SecurityHQ](https://www.securityhq.com/wp-content/uploads/2023/11/SecurityHQ-Infographic-5-Challenges-of-IoT-Security-and-Tips-to-Secure-Your-Devices.jpg)